Computer Security in Malaysia
Dr.
Wayne C. Summers
Associate
Professor - Computer Science
ITM-Pusat
Pendidikan Persediaan / MUCIA - Indiana University
Section
17, 40200, Shah Alam, Selangor, Malaysia
phone/fax:
(03) 541-5846
INTERNET:
wayne@cs.itm.my
Abstract: The use
of computer systems has improved our lives today. They have increased our efficiency of doing
work. We are now more productive, but at
a cost. We have become dependent on
these same computer systems in our daily lives and for doing business. Coupled with this is a lack of awareness of
how vulnerable our data, software and hardware are. This paper discusses the problems associated
with maintaining a secure computer system as well as proposing some solutions
to overcoming these problems. This paper
also summarizes the results of a series of surveys conducted in Malaysia by the
author. The surveys were used to
determine the status of computer security in Malaysia and provide a foundation
for suggesting some solutions to problems that are existent in Malaysian
computer security.
Introduction
"17,712 bank fraud cases
since 1986" [8]
"Police warn of 'computer
hackers' infiltrating CDS" [5]
"Computer virus to hit next
month - it will wipe out all hard disks every day of March" [4]
"Many users still ignore
rampant virus threat" [6]
"Blackout creates havoc for
IT users" [1]
"Subang Airport fire: A
lesson for IT users" [3]
These are some headlines from
recent Malaysian newspapers. Has your
company taken precautions to keep out hackers?
Are you ready for the next big virus attack? Can your business survive a lengthy power
outage? Could your company recover from
a major fire? These are some questions
that you may be facing in the future.
Information is the lifeblood of
every company. We have become
increasingly dependent on our computer systems for processing this
information. Not only must we protect
this information but we must also protect the computer systems that process
this information. There is a myriad of
threats to the security of our information and computer systems. Most computer users take the computer system
and the information it holds for granted.
They turn off their computers without giving any thought to the security
of the information.
Is
there a security problem in computing?
Computer Crime
One serious problem facing
computer users today is the rise in computer crime, i.e. crime committed with a
computer. Computer fraud in the U.S.
alone exceeds $3 billion each year. Computer
fraud in the U.K. exceeds 2.5 billion pounds each year. There was a total of 17,712 cases of bank
fraud involving 124.13 million ringgit in Malaysia between 1986 and
1992[8]. The total estimated losses due
to computer crime worldwide range from $300 million to $500 billion per
year. The reason for such a wide range
is that less than 1% of all computer crime fraud cases are detected and of
those detected, over 90% are unreported.
Is it any wonder that computer-related crime has been escalating at a
dramatic rate? Computer crime is almost
inevitable in any organization unless adequate protections are put in place.
|
Figure
1 |
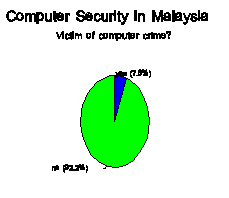
In recent surveys conducted in
Malaysia by the author [Appendix A], less than 8% of those surveyed had been
victims of a computer crime [Figure 1].
Unfortunately these 8% may be among the 1% detected. How many others "got away with
it?" Of those nine instances of a
computer crime, over 50% went unreported to the authorities and only one
individual was reported to have lost their job.
Crimes using computers are easy
to commit, hard to detect and even harder to prove. If someone steals your computer, you know it
and may even have evidence. If someone
steals your data, how do you know it and where's your proof. As will be discussed throughout this paper,
one major problem is a lack of awareness.
Few individuals and companies are aware of the extent of computer crime
committed today.
|
Figure
2 |
Computer Viruses
Computer viruses are a leading threat
to secure computing. There are over 3000
computer viruses and strains with several new ones developed every day. Over eight million PCs have been hit by
viruses by 1992 with 90% of those infected being reinfected within a short
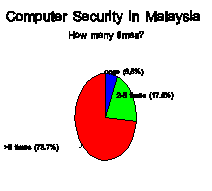
period. Over 90% of those surveyed in Malaysia have
experienced a computer virus infection [Figure 2]. Almost 74% of those had at least five
infections [Figure 3]. It's also
possible that some of those who claim to have not been infected by viruses, may
have not known how to recognize an infection.
|
Figure
3 |
Fortunately in Malaysia, the
number of virulent viruses is probably less than 100. Most of these are relatively harmless. One reasons for so many occurrences of
viruses both here and elsewhere is the widespread copying of software. Stop the illegal copying and use of illegal
software and the spread of viruses would diminish greatly.
Natural Disasters
Malaysia has the fortune to not
suffer from many natural disasters, but there are some. For example, within seven months last year the
Subang International Airport suffered two fires. The fire in April at Subang
International Airport knocked out the computers controlling the flight display
system. A post office near the DCA
computer room was also affected by the soot that decommissioned the post office
counter terminals. The computers were not burnt but crashed because soot
entered the hard disks. The fire in
October damaged newly installed computer equipment worth 400,000 ringgit as
well as 7 million ringgit worth of equipment in the air traffic control
tower[3].
Power outages are a regular
occurrence here culminating in the major blackout in September 1992. The
blackout crippled port operations when the Port Klang Authority's computer network
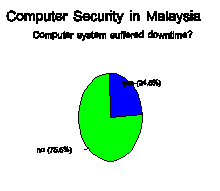
went blank[1]. Almost 25% of those
surveyed reported downtime due to a "natural disaster." [Figure
4] Most
of these were a result of power outages and hard disk crashes.
|
Figure
4 |
"Unplanned computer
downtime" costs Corporate America US$4 billion a year. An average U.S.
company suffers nine four-hour computer crashes a year, which each cost
US$330,000.
Negligence
Over 85% of the destruction of
valuable computer data involves inadvertent acts. This includes accidents, errors and omissions
by employees. This would typically
include accidental erasure of files or entire disks. Often employees may inadvertently alter files
beyond recovery.
HOW
MUCH SECURITY IS ENOUGH?
Computer Security
What is computer security? It can be thought of as the protection of the
computer and its resources against accidental or intentional disclosure of
confidential data, unlawful modification of data or programs, the destruction
of data, software or hardware. It includes the denial of use of one's computer
facilities for criminal activities including computer related fraud and
blackmail. Computer security involves
the elimination of weaknesses or vulnerabilities that might be exploited to
cause loss or harm. How can we minimize
the vulnerabilities in our computer system?
A computerized system for
processing information is composed of five major components: hardware,
software, data, people and procedures.
We need effective controls for all five components that will reduce the
system's vulnerabilities.
Data
Data is the most important of
the five components. It is the
life-blood of the company. The easiest
way to protect the data is to hide it from prying eyes. One way of doing this is by encryption. Encryption uses an algorithm that hides the
meaning of the text[Fig. 5].
plaintext ______ ciphertext ________
original
---------------->
|_______| -------------->|________| ----------->
plaintext
Figure
5
A good cryptographic algorithm
should be simple to use by authorized users but difficult and time consuming
for non-authorized users to decrypt. The security of the data should not depend
on the secrecy of the algorithm. The
efficiency and security of the algorithm should not be data dependent. More programs are appearing that include and
support encryption. Less than 40% of
those surveyed [Appendix A - Question 17] use encryption to hide their data.
Software
Software can be easily corrupted
by computer viruses. Computer viruses
typically infect executable programs, boot sectors and partition tables of hard
disks. Two major approaches can be used
to minimize the danger of infection.
One approach is to scan for
viruses. this won't stop the infection,
but it will notify you if an infection has occurred so that you can remove
it. To be effective, scanning must be
done any time new software is introduced into a computer system. The scanner must also be able to identify all
known viruses as well as viruses that were not released when the scanner was
designed. Most of those individuals
surveyed are using some type of scanner [Appendix A - Question 8] but nearly a
third seldom use it.
Another approach is to use a TSR
(Terminate and Stay Resident) program that will monitor for attempts by viruses to infect your system. The disadvantage of a TSR is that it might
give a false alarm if a legitimate program tries to do something similar in
characteristic to a virus's action.
Malaysia is fortunate that there are three excellent local products
(V-buster, PC-Medic and Armour) which have both scanners and TSR programs. The advantage of a local product is that the
development team should have access to viruses that are creating the most havoc
locally and design the anti-virus program for that. There are also many imported scanners and TSR
programs. Many users are using more than
one product to combat viruses.
The next level of software
protection are the Access Control Systems.
ACS's lets you selectively restrict access to files, directories, floppy
disk drives, and even external ports.
Many systems can also track program use through logging and audit
trails. ACS's should also include encryption facilities. Some ACS's can also make the hard disk drive
"inaccessible" on a boot from a floppy. Some examples of Access Control Systems
include Watchdog, PC-FORT( which is a well written program by a
team of Malaysians), DiskLock, and PC/DACS.
ACS's won't prevent an
experienced programmer from looking at the raw disk sectors. Most ACS's also won't prevent a user from
doing a low-level format from a floppy disk drive.
Access Control Systems usually
include some type of password protection to control access to different parts
of the computer system. These provide a
very important line of defense.
Passwords are easy to use but also easy to misuse. Many computer users either select passwords
that are not only easy to remember but also easy to guess by an intruder. Other users select a password that is so hard
to remember that they have to write it down where the intruder can find it.
Some rules of thumb for
passwords include selecting a password that is over five characters long
containing upper and lowercase letters, digits and punctuation characters if
possible. Pick a password that can be
easily memorized but not easily guessed.
Don't share it with everyone.
Passwords can accidently be divulged over time, so they should be
changed periodically. Many application
packages also have password protection options for the data files, but few
individuals are using them.
Hardware
How valuable is your computer,
your printer, your monitor, etc.? You
could bolt it to the desks like a quarter of those surveyed [Appendix A -
Question 23]. You could put in a limited
access room like 60% of those surveyed [Appendix A - Question 25]. Computers are very sensitive electrical
devices and need to be protected from electrical surges. Surprisingly, 28% of those surveyed [Appendix
A - Question 26] do not use voltage regulators or surge protectors. With the frequent fluctuations of current in
Malaysia, which is a gamble you're sure to lose on.
If you cannot afford to have
your computers or network going down unexpectedly, then you should invest in a
UPS (Uninterruptible Power Supply). 60%
of those surveyed [Appendix A - Question 27] use UPSs.
People and Procedures
Computers do not commit crimes
and computers do not write computer viruses.
Most of the problems associated with computer security are people
problems. These problems can generally
be solved with appropriate procedures.
Establish a computer security policy and educate the users about the
procedures they are expected to follow.
A good computer security program involves everyone in the organization
from senior management down. Over 50% of
those surveyed [Appendix A - Question 14] state that their company has no
computer security policy. It is
important that computer users understand the issues of computer security,
computer ethics as well as the legal issues involved in using a computer.
|
Figure 6 |
Procedures must be developed for
using secure computing systems. Users
must not leave PCs unattended without securing both the PC and any storage
media. Printers should not be left
unattended when printing confidential information. Secure all software and hardware with
passwords and if possible lock and key.
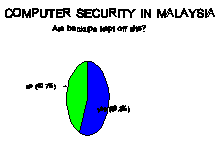
It is ironic that 75% of those surveyed [Figure 6] lock up their office
supplies while over 50% [Figure 7 & 8] leave their software and data unsecured
at night. Are paper clips and pencils
more important than our data?
|
Figure 7 |
|
Figure 8 |
Do not allow eating, drinking
and smoking near the computers. Computer
personnel in mainframe and minicomputer environments recognized early the
importance and necessity of placing the computer and storage media in a clean
environment. Unfortunately, this concern
is lost when we move to PCs and networks.
|
Figure 9 |
Backup
One most important procedure to
establish is the one of backup. Data and
software can be lost due to a virus attack, sabotage or by negligence. It is necessary to have current backups to
recover from the loss. Where should
those backups be kept? Although most of
those surveyed [Figure 9] made regular backups, over 40% keep the backups on
site with the computer. If a disaster
were to suddenly strike the computing facility, not only is the computer and
original data lost, but so is the backup.
Mainframe computer personnel have procedures for keeping two generations
of backups. The first is kept on site
while the second generation of backups is kept in another building preferably
far away.
|
Figure 10 |
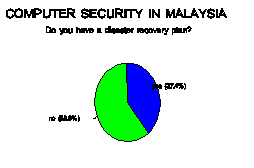
Contingency Planning
How long can you survive without your
computers? Studies have shown that over
90% of the companies that suffered a "catastrophic loss" in their
computer systems never recover. You must
plan for the unlikely. Unfortunately, of
those surveyed [Figure 10], less than 40% have a disaster recovery plan.
Malaysia is very fortunate in
having two facilities available for disaster recovery. One is the Computer
Recovery Facility in Kelana Jaya while the other is the Computer
Recovery Center in Petaling Jaya.
Both companies provide security facility for storing off-site
backups. In addition both companies
provide both "cold site" (Shell) and "hot site"
facilities. The cold site provides
power/cooling and should be up and running within a week. The hot site is a complete hardware
facility and only requires that the
software and backups be installed before you can start operating.
An alternative to these
facilities is to have your own hot or cold site where all processing is
mirrored so that you can recover immediately from a disaster. Some companies will even share
facilities. Of course the disadvantage is cost. But then, how dependent are you on your
computer systems? Computer security does
not come cheap.
RECOMMENDATIONS
Here are some final
recommendations. Keep the hardware,
software and data in a secure place.
Don't leave your PC unattended.
If you are in a network environment, log off before leaving your
computer or terminal. Protect your
software with some type of anti-virus software.
Invest in an access control system.
This will provide you with password protection for your files and
devices. Access control systems can also
keep track of who is doing what on your computer system. Protect your data using encryption. That way if some one does break into your
system, your data is still secure.
Design a security plan and
define policies to be followed by all computer users. Educate employees about legal and ethical
issues involving the use of computers.
Do not allow anyone to use their own software on the company computers,
especially pirated software. Do not
allow any one to remove software or data from the workplace. Educate all computer users about the
importance of computer security.
Create a security planning team
with 5-9 members. These should include
members from the computer hardware group, data entry personnel, systems
programmers, application programmers, physical security personnel and
representative users. Make sure that
senior management is involved in setting this up and are supportive of this
group's efforts. If senior level
management does not see the importance of computer security, all may be lost.
When designing a security plan,
consider the following:
-
specify goals regarding security
-
specify where responsibility for security lies
-
specify the organization's commitment to security
-
identify current security status
-
make recommendations
-
identify responsibilities for implementation
-
draw up a timetable
-
provide continuing attention to security
-
involve senior level management.
FUTURE
OF COMPUTER SECURITY IN MALAYSIA
Computers are becoming more
secure in Malaysia. Through conferences
and seminars like NCIT, there is an increased awareness that computer security
is important. Both the private sector
and the government frequently offer programs on computer security. There is currently an organization, MITSA -
Malaysian Information Technology
Security Association being registered which has as one of its goals to
educate computer users and industry about the issues involving computer
security.
New laws are being established
to combat computer crime. In August, the
Malaysian Law Minister, Datuk Syed Hamid Albar tabled a Penal Code Amendment
Bill that increases the penalties for white-collar crime including computer
crime. Most importantly is that the Bill
expands the definition of the word "document" to include data stored
magnetically. This will now make
stealing data easier to prosecute.
More companies are taking
advantage of disaster recovery facilities.
Some are setting up their own while other companies are making use of
the two in existence. Bank Negara is
insisting that all financial institutions make use of disaster recovery
facilities. They also require that the
disaster recovery plan and facility be tested frequently. This is important. Each company needs to educate its employees
on what to do in an emergency.
These developments and new ones
on the horizon will hopefully make our computing more productive and
safer. Keep your computer system secure
and practice safe computing.
References
1. CompuTimes, New Straits
Times newspaper, "Blackout creates havoc for IT users," Malaysia, October 5, 1992, pg. 1.
2. Fites, Philip E., Kratz,
Martin P.J. and Brebner, Alan F., Control and Security of Computer
Information Systems, Computer Science Press, Rockville (MD), 1989.
3. IT Asia, "Subang Airport fire: A
lesson for IT users," November, 1992.
4. Malay Mail newspaper,
"Computer virus to hit next month - it will wipe out all hard disks every day of March," Malaysia,
February 24, 1993.
5. New Straits Times
newspaper, "Police warn of 'computer hackers' infiltrating CDS," Malaysia, May 26, 1993, pg. 4.
6. PC Week Asia,
"Many users still ignore rampant virus threat," May 8-21.
7. Pfeeger, Charles P., Security
in Computing, Prentice- Hall, Englewood Cliffs (NJ), 1989.
8. Star newspaper,
"17,712 bank fraud cases since 1986," Malaysia, September 8, 1992.
9. Stoll, Cliff, The Cuckoo's
Egg: Tracing a Spy Through the Maze of Computer Espionage, Doubleday, New
York (NY), 1989.
10. Summers, Wayne C. seminar
notes for "Computer Security, Computer Crime and Combatting Computer
Viruses," April 1993.
11. Summers, Wayne, Zaidah
Ibrahim and Naimah Mohd. Hussin, COMPUTER VIRUSES: What They Are and How to
Prevent Them, Federal Publications, Malaysia, 1993.
Appendix
A
COMPUTER
SECURITY IN MALAYSIA
Location: INTAN EXCELL EXCELL MCCE MCCE
PC‑Fort Totals
K.L. K.L. Penang K.L. Sabah Launch
Date: 8/1992 4/ 1993 4/1993 4/ 1993 8/
1993 5/1993
# of respondees: 55 11 8 6 23 26 129
1. Type of Company:
Gov't/Semi‑Gov't 43 1 2 1 6 53 41.09%
Education 9 3 22 5 39 30.23%
Banking 1 2 8 11 8.53%
Computer Related
1 2 1 1 5 3.88%
Oil 1 1 0.78%
Manufacturing 5 7 12 9.30%
Trading 3 3 2.33%
Services 1 4 5 3.88%
2. Number of Employees:
1‑10 3 2 5 3.40%
11‑99 12 3 2 12 10 39 26.53%
100‑999 22 7 6 3 9 7 54 36.73%
>1000 18 1 22 8 49 33.33%
3. Number of Computers:
1‑10 7 1 2 12 2 24 19.35%
11‑99 27 3 8 3 9 14 64 51.61%
100‑999 15 5 6 26 20.97%
>1000 4 2 4 10 8.06%
4. Type of Computers:
PCs 55 11 7 6 23 25 127 98.45%
minicomputer 24 10 2 1 13 50 38.76%
mainframe 33 4 1 10 48 37.21%
network 19 8 6 18 51 39.53%
5. Have you
experienced a computer virus infection?
yes 45 11 8 6 19 23 112 90.32%
no 10 0 0 0 2 0 12 9.68%
5a. If yes how many times?
once 2 1 4 3 10 8.77%
2‑5 times 5 3 2 4 6 20 17.54%
>5 times 38 8 7 4 13 14 84 73.68%
6. Is there an individual to contact in case of a
computer infection?
yes 35 9 6 1 8 20 79 61.24%
no 16 2 2 5 13 6 44 34.11%
7. Do you use a TSR to monitor for computer virus
infections?
yes 19 6 4 3 4 15 51 39.53%
no 24 4 4 2 12 11 57 44.19%
8. What type of antivirus program are you using?
Vbuster 11 1 6 2 20 15.50%
Scan 36 4 5 4 14 16 79 61.24%
CPAV 23 4 2 2 2 14 47 36.43%
NAV 8 4 1 1 2 3 19 14.73%
Dr. Solomon 6 1 1 8 6.20%
TNT 11 2 1 3 1 18 13.95%
UTipac 1 2 4 7 5.43%
Pc‑cillin 17 5 2 2 10 36 27.91%
PC‑Medic 5 5 3.88%
Armour 1 5 6 4.65%
Serum 1 1 0.78%
Lan Protect 1 1 0.78%
None 3 3 2.33%
9. How often do you scan for viruses?
daily 24 5 4 2 15 50 38.76%
weekly 13 3 4 3 5 3 31 24.03%
monthly 2 3 1 6 4.65%
seldom 14 4 1 10 6 35 27.13%
never 1 1 3 5 3.88%
10. Has your computer system suffered downtime due to
a natural disaster?
yes 11 3 1 2 4 6 27 24.55%
no 31 8 7 4 16 17 83 75.45%
11. How often do you make backups?
daily 16 7 7 2 1 12 45 34.88%
weekly 25 7 2 1 4 8 47 36.43%
monthly 6 4 1 1 5 2 19 14.73%
quarterly 2 2 1 1 6 4.65%
yearly 1 1 2 1 3 8 6.20%
seldom 3 4 7 5.43%
never 5 5 10 7.75%
11a. Are these backups kept off site?
yes 28 7 3 4 10 18 70 59.32%
no 20 4 8 2 6 8 48 40.68%
12. Does your company have a disaster recovery plan?
yes 19 7 1 0 2 17 46 37.40%
no 31 4 7 6 21 8 77 62.60%
13. Does your company have a security evaluation team?
yes 18 6 1 1 2 16 44 35.20%
no 34 5 7 5 21 9 81 64.80%
14. Does your company have a computer security policy?
yes 20 10 2 2 2 19 55 45.83%
no 28 1 6 4 20 6 65 54.17%
15. Does your company educate your employees about the
importance of
computer security?
yes 32 10 6 2 2 22 74 59.20%
no 21 1 2 4 20 3 51 40.80%
computer ethics?
yes 23 9 3 2 0 23 60 50.85%
no 27 1 5 3 20 2 58 49.15%
computer viruses?
yes 31 8 5 3 8 24 79 64.23%
no 22 3 3 2 13 1 44 35.77%
16 Are your computers protected with passwords?
yes 27 9 8 2 6 18 70 55.12%
no 28 1 0 5 16 7 57 44.88%
16a. How often are they changed?
weekly 2 1 3 6 11.54%
monthly 6 4 1 6 17 32.69%
quarterly 2 1 3 5.77%
seldom 4 2 2 8 15.38%
never 6 2 3 1 2 4 18 34.62%
17. Are your sensitive data files encrypted?
yes 17 6 2 1 3 14 43 38.05%
no 28 4 6 5 18 9 70 61.95%
18. Do you keep a log of computer usage?
yes 14 6 4 4 7 9 44 36.36%
no 36 5 4 2 15 15 77 63.64%
19. Are employees allowed to take software/data home
with them?
yes 26 2 2 3 15 4 52 40.31%
no 27 9 6 7 8 20 77 59.69%
20. Are employees allowed to use their own software in
the workplace?
yes 32 1 2 3 18 7 63 49.61%
no 22 10 6 3 4 19 64 50.39%
21. Is your software locked up at night?
yes 27 6 3 3 7 12 58 46.40%
no 26 5 5 3 16 12 67 53.60%
22. Is your data locked up at night?
yes 28 7 2 2 7 13 59 47.58%
no 25 4 6 4 15 11 65 52.42%
23. Is your hardware bolted down?
yes 9 3 1 0 8 2 23 22.33%
no 30 8 6 5 11 20 80 77.67%
24. Are your office supplies locked up?
yes 40 10 7 5 14 17 93 76.86%
no 12 1 1 0 6 8 28 23.14%
25. Are your computing facilities in a limited access
room?
yes 29 8 6 3 15 12 73 60.33%
no 21 3 2 3 7 12 48 39.67%
26. Do you use voltage regulators/surge protectors?
yes 32 9 8 4 14 16 83 71.55%
no 14 2 0 2 6 9 33 28.45%
27. Do you use uninterruptable power supplies(UPS)?
yes 31 10 8 2 5 16 72 59.50%
no 23 1 0 3 13 9 49 40.50%
28. Have you been a victim of computer crime?
yes 2 1 0 2 2 2 9 7.76%
no 46 10 8 2 18 23 107 92.24%
28a. If yes was
it reported to the authorities?
yes 0 1 2 0 1 4 44.44%
no 2 0 0 2 1 5 55.56%
28b. What
happened to the suspect?
fired 1 1
arrested 0
convicted 0
warning 1 1 2
29. Do you have procedures for reporting and handling
computer crime?
yes 10 5 1 0 1 7 24 19.67%
no 42 6 7 6 19 18 98 80.33%